In an age where digital connections shape our daily experiences, the security of our applications is paramount.
One could even argue that our favorite apps are like the castles of the medieval era – only instead of moats and drawbridges, they’re fortified with firewalls and encryption.
And as much as you love diving into the latest mobile games or browsing top entertainment platforms, according to Sports Lens, it’s the invisible shields that keep the fun going without a hitch.
Let’s take a journey into the world of cybersecurity, delving into the safeguards protecting those apps you tap into every day.
The Wall of Fire: Firewalls
When it comes to cybersecurity, the firewall is your app’s first line of defense and plays a crucial role in the safety of digital platforms.

Much like a physical wall that repels unwanted visitors, a firewall operates diligently to oversee the safety of your digital interactions.
It meticulously monitors and controls both the incoming and outgoing network traffic using well-established security guidelines.
These predetermined security policies are put in place by experts who anticipate some of the biggest cybersecurity threats.
This rigorous system ensures that harmful data, which can range from malware to aggressive hacker attempts, is kept at bay.
On the other hand, legitimate and safe traffic, which users want and expect, is allowed to flow through without any hitches, ensuring a smooth and secure user experience.
Coded Secrets: Encryption
Imagine sending a letter that only the intended recipient can read, while to the outside world, or to anyone else who might intercept it, it looks like a series of incomprehensible symbols.
That’s the magic and practicality of encryption in a nutshell. Just as you’d want your personal letters to be private, you’d expect the same for your digital data. When information is encrypted, it undergoes a process where it’s turned into a scrambled code.
To revert it back to its original form or understand its content, one needs a unique key. Without this key, the encrypted data remains unreadable.
Many of the apps you use daily, from messaging platforms to banking apps, leverage this encryption technology. They understand the importance of safeguarding users’ data.
So, every time you send a message or check your bank balance, these apps utilize encryption methods to keep your personal and financial information away from prying eyes, ensuring it stays strictly confidential.
Constant Vigilance: Regular Updates
Updates might seem pesky and even a tad annoying when they suddenly pop up and interrupt your app usage, particularly when you’re in the middle of something important. However, these updates are more crucial than they may initially appear.
Developers and software teams work tirelessly behind the scenes, often combing through lines of code and user feedback, searching for vulnerabilities or potential areas of exploitation in their apps.
Once they identify these weak points, they work diligently to fix or “patch” them, ensuring these gaps are sealed. And just like that, with some effort and technical magic, an update is made available for users.
By regularly updating your apps, not only do you get new features or improved performance, but more importantly, you ensure that your devices are armed with the latest defenses against any emerging cyber threats. It’s always better to stay a step ahead and keep those updates coming.
The Guard At The Door: Authentication Protocols
How does an app ensure that you, and only you, can access your personal space, especially in a world where data breaches seem all too common? The answer lies in smart security measures called authentication protocols.
Essentially, these are well-designed processes put in place to confirm the user’s identity, ensuring that only authorized individuals get through. In recent years, one method has stood out and gained significant traction: two-factor authentication, commonly known as 2FA.
The beauty of 2FA is in its simplicity and effectiveness. Initially, users will enter their regular password, something they know. But, to add an extra layer of security, they’re then prompted to provide a second piece of evidence.
This could be a unique code sent via text to their phone or generated by a specific app. By asking users for two distinct forms of identification, the system ensures a higher level of security.
This double-checking mechanism acts as a sturdy barrier, making it considerably harder, if not nearly impossible, for unwanted guests or malicious actors to sneak into your digital sanctuary.
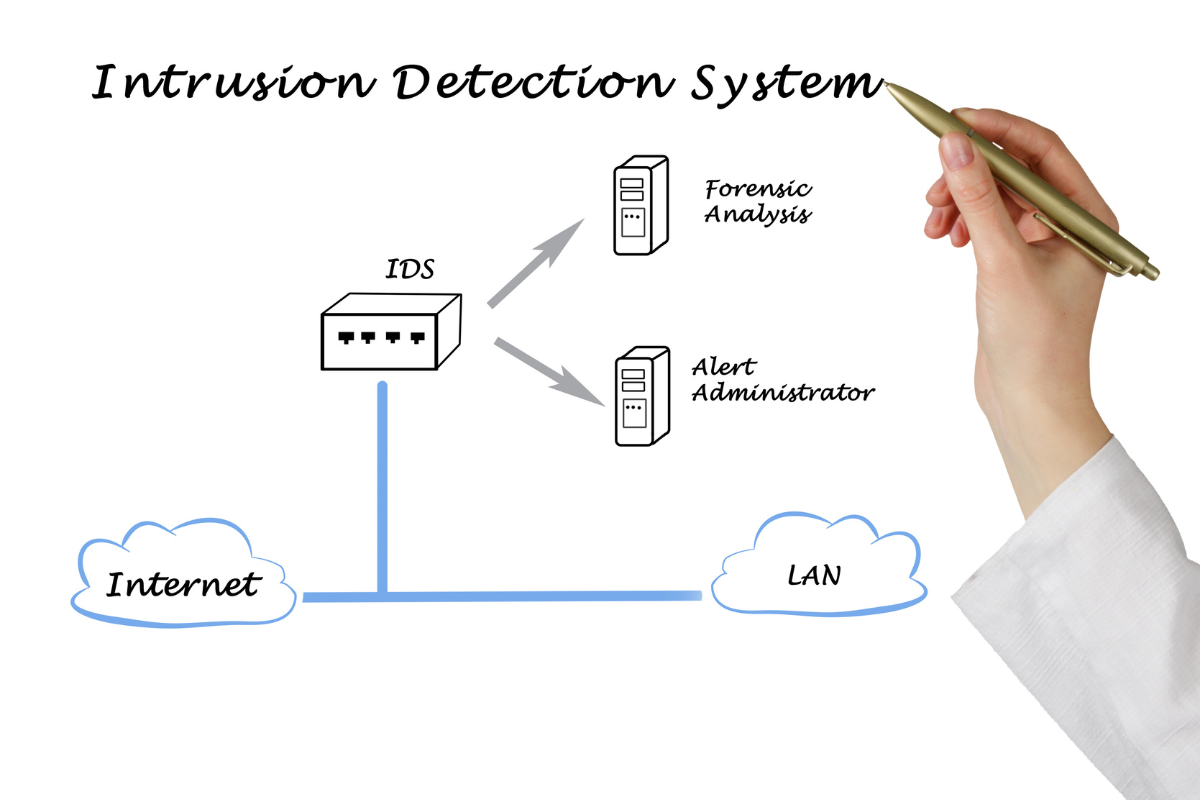
The Watcher In The Shadows: Intrusion Detection Systems (IDS)
While we all wish and genuinely hope that unwanted visitors, like hackers or malware, never breach our defenses, it’s always wise to be prepared. Think of it as having a vigilant security guard who never sleeps.
It’s this very reason that many systems incorporate an Intrusion Detection System, or IDS for short. Acting like a digital watchdog, the IDS tirelessly monitors all network traffic, scanning every bit of data that comes and goes.
For instance, if there’s a sudden surge in data requests or an unfamiliar IP address trying to access the system repeatedly, the IDS takes notice.
If it identifies anything that seems out of the ordinary or potentially harmful, it doesn’t remain silent. The IDS immediately sends out an alert to the system administrators or the relevant team.
This prompt alerting mechanism ensures that there’s ample time to take quick action, whether that’s blocking a suspicious source or fortifying the defenses further, ensuring the system remains uncompromised and safe.
Protecting The Realm: Continuous Monitoring
Last but not least, behind the scenes of most well-protected apps is a dedicated team of cybersecurity professionals, often working around the clock.
These experts have extensive training and expertise in identifying and tackling various cyber threats. They don’t just passively observe; they actively and continuously monitor the app’s environment, analyzing data and checking for any anomalies.
By leveraging advanced tools and their vast knowledge, they keep a keen eye on potential vulnerabilities. Their proactive approach means that they don’t just react to threats; they often anticipate them.
By staying vigilant and always being on their toes, they can quickly spot any irregularities or potential dangers. This timely detection allows them to address and neutralize threats well before they escalate into significant problems.
In Conclusion
As you swipe, tap, and scroll through your favorite apps, it’s comforting to know a plethora of measures are working behind the scenes to keep your digital experience secure.
The world of app security is vast, and while we’ve only scratched the surface today, it’s evident that developers go to great lengths to ensure you can enjoy their creations without a worry.
So, the next time an app asks you for an update or a second authentication step, remember: it’s all part of the grand design to keep your digital kingdom safe and sound.